10 Facts About Business Email Compromise That You’ve Got to See

These Facts About Business Email Compromise Show Just How Dangerous It Is
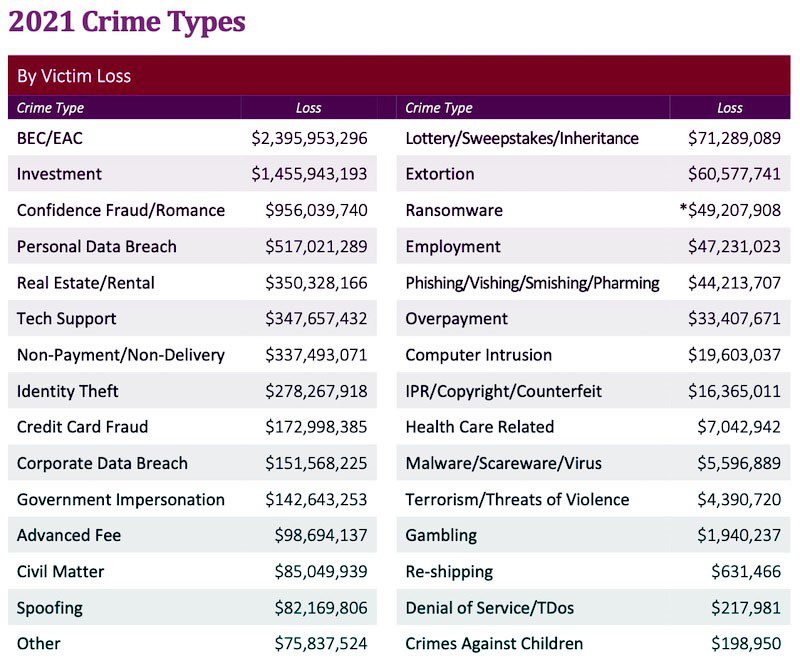
What’s the most expensive cyberattack that businesses face today? If you said business email compromise (BEC) you’re right. The FBI IC3 2021 Internet Crime Report showed that BEC packed a powerful punch against U.S. businesses that year. BEC complainants to IC3 suffered $2,395,953,296 in losses in 2021, 28% higher than 2020’s record total of $1,866,642,107. These 10 facts about business email compromise can help you gain insight into the scope of this dangerous cyber risk for businesses.

See cybercrime trends & the results of thousands of phishing simulations in The Global Year in Breach 2022. DOWNLOAD IT>>
10 Facts About Business Email Compromise That You’ve Got to See
- Business email compromise schemes have caused at least $5.3 billion in total losses to approximately 24,000 enterprises in the U.S. in the last 3 years.
- More than 70% of organizations have experienced a BEC attack.
- The U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) named business email compromise a cyberattack that is 64x worse for businesses than ransomware
- Nearly 50% of all BEC attacks result from the spoofing of an individual’s identity.
- 68% of BEC attempts involve spoofing an organization
- 53% involve masquerading as a boss or executive in the target’s company
- 66% of BEC attempts address their target by name
- 77% of organizations faced business email compromise attacks in 2021, up from 65% in 2020. That represented an 18% increase in BEC attacks.
- BEC losses involving cryptocurrency achieved the highest numbers to-date in 2021 with just over $40M in exposed losses.
- Phishing/BEC/Smishing was responsible for the highest number of data compromises in H1 2022.

Get a step-by-step guide to building an effective security and phishing awareness training program. GET GUIDE>>
What is Business Email Compromise?
Business email compromise (BEC) is a cyberattack in which cybercriminals utilize seemingly legitimate (or freshly stolen) email accounts from another organization to fraudulently trick employees of another business into giving them credentials, money, personal information, financial details, payments, credit card numbers or other sensitive data. BEC attacks grew by 84% per inbox in 2022.
What Are Some Types of Business Email Compromise Scams to Be on the Lookout for?
Business email compromise is not a one-size-fits-all proposition. It is especially tricky to spot because it is a scheme that can take many forms.
Urgent payment required scams
Fake invoice scams are the most common BEC variation. In this scenario, someone with the authority to pay vendors in an organization is sent a legitimate-looking invoice from a company that their organization does business with demanding immediate payment to avoid loss of goods or services. Spear phishing is the most common vector for these scams.
Gift cards and wire transfers
Money is the goal behind BEC. Cybercriminals will typically demand that payment for fraudulent reasons be transferred to them via wire transfer, cash app or gift card. An estimated 62% of BEC scams involve the cybercriminal asking for gift cards, cash app transfers or money cards. Many of today’s wire transfer scams utilize cryptocurrency.
Credential compromise scams
In this BEC variant, fraudsters will ask for the victim to provide credentials for a business account or access to a company’s systems or data, often on the pretense that they’ve misplaced credentials or weren’t given the right ones to complete a task. Sometimes bad actors will pose as tech support or customer service personnel from a service provider.

The Guide to Reducing Insider Risk can help IT pros stop security incidents before they start! GET IT>>
Business Email Compromise in Relation to Other Cyberattacks

Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
Business Email Compromise and Its Relationship with Phishing
It pays to learn the facts about business email compromise and what it looks like in action.BEC scams often start with phishing. It’s an easy and cheap way for bad actors to get the ball rolling for most of today’s nastiest cyberattacks. Phishing is popular because it works, and employees are facing a flood of phishing threats every day. The number of recorded phishing attacks hit an all-time high in Q1 2022, with more than one million attacks in a quarter recorded for the first time. Phishing lures that are part of a BEC attack are often sophisticated, making it hard for employees to handle. An estimated 97% of employees cannot detect a sophisticated malicious message.
FBI IC3 Tips for Avoiding BEC
- Use secondary channels or two-factor authentication to verify requests for changes in account information.
- Ensure the URL in emails is associated with the business/individual it claims to be from.
- Be alert to hyperlinks that may contain misspellings of the actual domain name.
- Refrain from supplying login credentials or PII of any sort via email. Be aware that many emails requesting your personal information may appear to be legitimate.
- Verify the email address used to send emails, especially when using a mobile or handheld device, by ensuring the sender’s address appears to match who it is coming from.
- Ensure the settings in employees’ computers are enabled to allow full email extensions to be viewed.
- Monitor your personal financial accounts on a regular basis for irregularities, such as missing deposits.
- If you discover you are the victim of a fraud incident, immediately contact your financial institution to request a recall of funds. Regardless of the amount lost, file a complaint with www.ic3.gov or, for BEC/EAC victims, BEC.ic3.gov, as soon as possible.

Finding the fix for your security & compliance training challenges is easy with our buyer’s guide! GET YOUR GUIDE>>
Reduce BEC Risk with Security Awareness Training & Phishing Simulations
One of the most effective weapons against phishing is regular security awareness training. This multi-benefit dynamo slashes the chance that employees will fall for a phishing lure dramatically. In fact, 80% of organizations in a study said that security awareness training reduced the chance that a staffer would fall for phishing substantially. Ultimately researchers determined that although security awareness training doesn’t work overnight, it makes steady progress that holds up over time reducing a company’s phishing risk from 60% to 10% within the first 12 months.
Beyond training with videos and quizzes (the most effective type of security awareness training), training employees to resist the temptations of phishing lures using phishing simulations is an effective tactic. In a report by Microsoft, analysts determined that when employees receive simulated phishing training, they’re 50% less likely to fall for phishing. People are more likely to learn and retain new knowledge by experience, and phishing simulations help employees hone their ability to spot red flags – and an estimated 90% of employees who receive more than five minutes of security awareness training every month are likely to know to divert suspicious messages to administrators or the IT team.

Go inside nation-state cybercrime to get the facts and learn to keep organizations safe from trouble! GET EBOOK>>
Training Employees to Resist BEC is Easy and Affordable with BullPhish ID
BullPhish ID is the ideal solution for businesses to use to train employees to resist BEC attacks as well as malware, spear phishing and credential compromise. It is the industry leader in phishing simulations. These features help ensure that employees quickly gain cybersecurity knowledge and compliance skills while developing their phishing resistance fast to protect organizations from phishing-based cybercrime.
- Choose from a wide variety of plug-and-play phishing simulations, with new phishing simulation kits added every month.
- Train your way with fully customizable phishing kit content including links and attachments to reflect industry-specific threats.
- Access a huge library of security and compliance training videos with 4 new videos added every month on topics like BEC, CMMC compliance, data handling and more.
- Quickly measure retention and see who needs more help with quizzes and easy-to-read progress reports.
- Security and compliance training videos are available in 7 languages!
NEW FEATURE! Enjoy a major BullPhish ID enhancement, Advanced Phishing Simulations (Drop-A-Phish), that leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users. LEARN MORE>>

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!